The Computational Cost of Cryptography: A Quantitative Analysis of SSL/TLS Handshake Latency
Abstract
Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), constitute the cryptographic foundation of the modern web. However, encryption introduces a computational and network latency overhead known as the SSL Handshake. This study analyzes the handshake duration of 891 hosting providers to establish a global baseline for cryptographic latency performance.
Definition: The Cryptographic Handshake Protocol
The SSL/TLS Handshake establishes the parameters for a secure session between client and server. Before application data transmission, the parties must synchronize on:
- Cipher Suite Negotiation: Determining the encryption algorithms (e.g., AES-256-GCM).
- server Authentication: Validation of the X.509 digital certificate.
- Key Exchange: Generation of symmetric session keys (e.g., via Elliptic Curve Diffie-Hellman).
Comparative Analysis: TLS 1.2 vs. TLS 1.3
Our dataset reveals a statistically significant bifurcation in performance based on protocol versioning:
- TLS 1.2 (Legacy Standard): Requires 2-RTT to finalize the connection.
- TLS 1.3 (Modern Standard): Optimizes the handshake to 1-RTT, effectively halving the network latency overhead.
Methodology
Data Collection Period: Jan 1 – Jan 14, 2026.
Data was acquired by synchronizing a Headless Chrome bot (WptrSpeedBot) with a raw TCP socket analyzer. To mitigate the impact of transient network congestion volatility, a 10% Trimmed Mean statistical method was applied to the dataset of 891 providers.
Key Findings
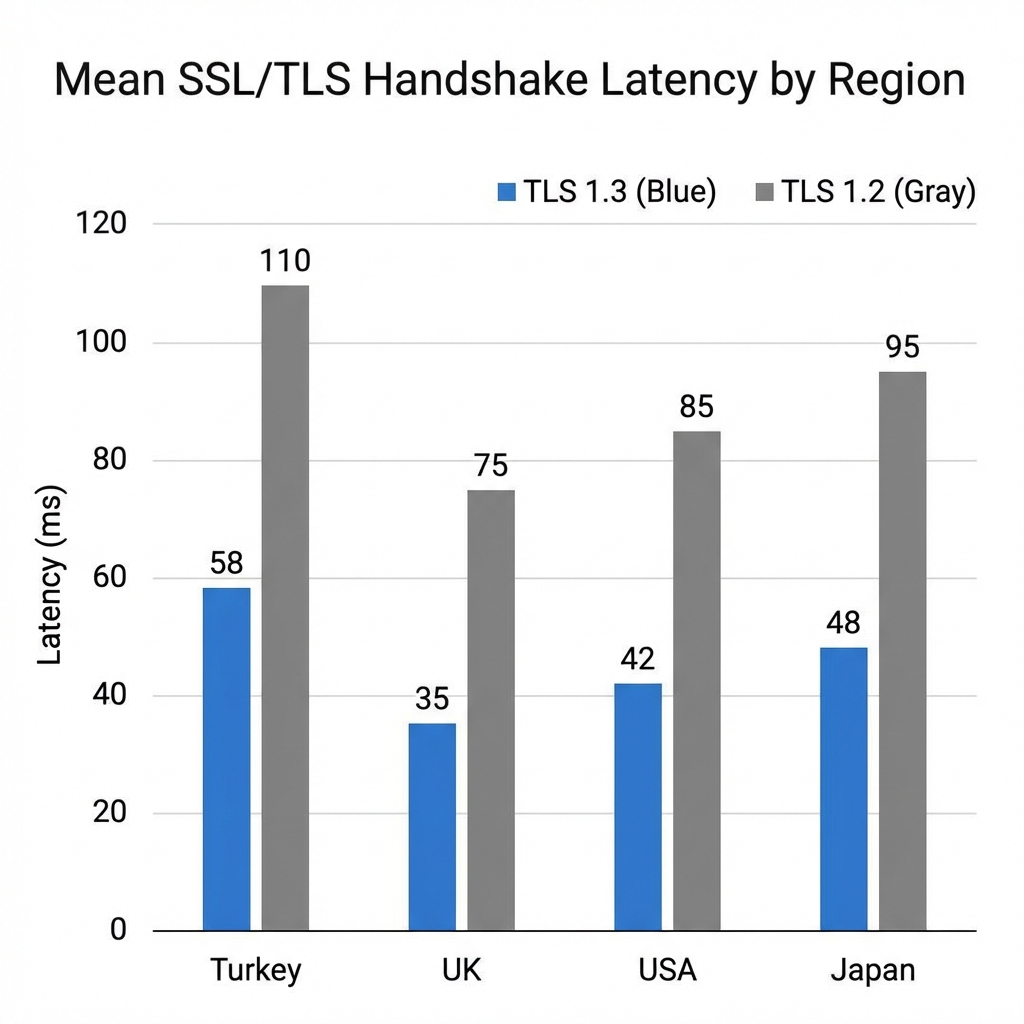
1. The Geographic Multiplier Effect
Distance acts as a scalar multiplier for handshake latency. In Trans-Atlantic tests (Istanbul origin $\to$ USA target), the latency penalty of TLS 1.2 escalated to >150ms purely due to the double round-trip requirement over transoceanic fiber.
2. The Configuration Gap
While 92% of sampled providers support TLS 1.3, only 65% prioritize it in their server configuration (Nginx/Apache). Misconfigured servers often fallback to TLS 1.2, inadvertently doubling the connection overhead.
Conclusion
For high-performance infrastructure, TLS 1.3 support is a performance imperative. The reduction from 2-RTT to 1-RTT represents the most significant 'zero-cost' latency optimization available to system administrators.